Bypass
First HTB challenge completed! Difficulty: Easy
Want to take a go for yourself first? You can find the challenge here.
Quick background
I’ve always tried learning reverse engineering in the past but I’ve found it very hard to start because I thought it just consisted of reading lines of assembly using Ghidra for every application and I never knew how to even remotely read assembly at the time. So, I’m now trying to get back into learning it. The more challenges I solve, the more I’ll get experience in how to start, where to look and build some methodology when solving reversing challenges.
Solving process
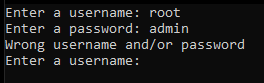
The program is simple, it’s a login page and its likely that we need to find the correct username and password to get the flag.
I initially imported the program in Ghidra, in which, I was immediately overwhelmed with where to start or how to read any of the assembly. Even the decompiled code preview wouldn’t help me (It looks like it needed to load the address of MSCOREE.DLL, a part of the program to do that possibly). I do know that I had to look for the entry function (Ghidra already shows you where it is) and I found that the program has 8 functions, but that’s as far as I got.
Ghidra wasn’t the solution, so I thought I’d just decompile the program. I used JetBrains dotPeek to do it, and it did give me much more readable code. But from static analysis, it just shows this program will always be in an infinite loop.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
using System;
public class 0
{
public static string 0;
public static string 1;
public static string 2 = 5.8;
public static void 0()
{
if (0.1()) // Go to function 1(), if return value is true then continue
{
0.2();
}
else
{
Console.WriteLine(5.0);
0.0(); // Infinite loop
}
}
public static bool 1()
{
Console.Write(5.1);
Console.ReadLine();
Console.Write(5.2);
Console.ReadLine();
return false; // Always returns false
}
}
So I definitely needed a debugger too. I conducted some research online about what software I could use for reverse engineering PE applications (.exe) and I came across 2 popular tools, x64dbg (which I’ve never used before) and dnSpy (which I know but used little). I went ahead and installed dnSpy, I imported the file and it seemed to decompile it much better than dotPeek.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
using System;
public class 0
{
public static void 0()
{
bool flag = global::0.1();
bool flag2 = flag;
if (flag2)
{
global::0.2();
}
else
{
Console.WriteLine(5.0);
global::0.0();
}
}
public static bool 1()
{
Console.Write(5.1);
string text = Console.ReadLine();
Console.Write(5.2);
string text2 = Console.ReadLine();
return false;
}
public static void 2()
{
string <<EMPTY_NAME>> = 5.3;
Console.Write(5.4);
string b = Console.ReadLine();
bool flag = <<EMPTY_NAME>> == b;
if (flag)
{
Console.Write(5.5 + global::0.2 + 5.6);
}
else
{
Console.WriteLine(5.7);
global::0.2();
}
}
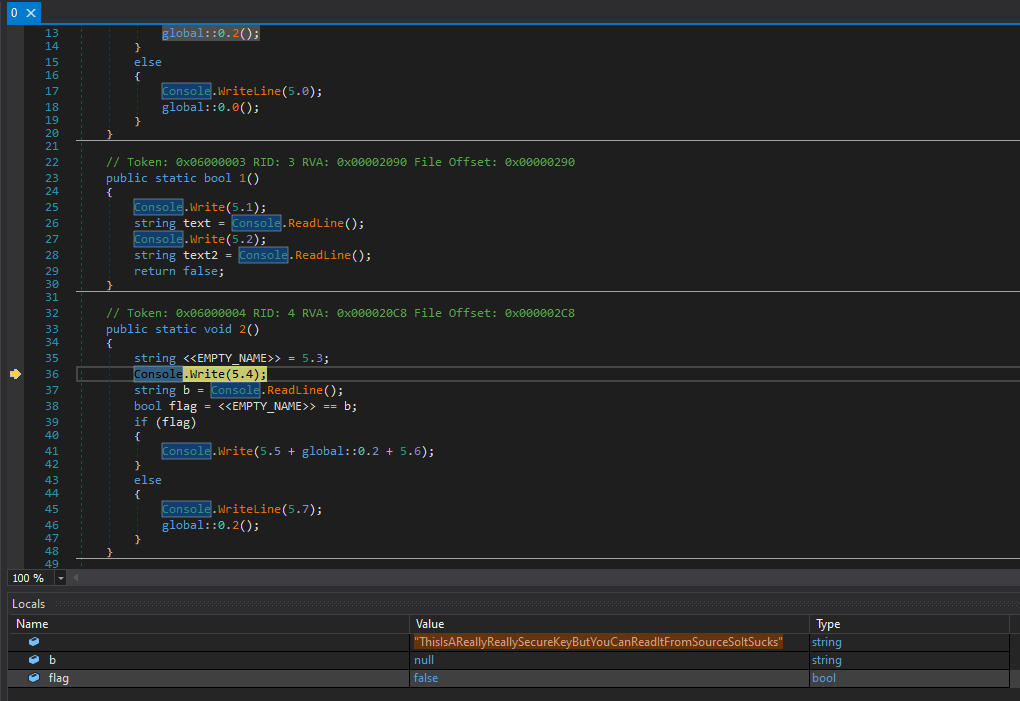
I was initially stuck on how to solve this infinite loop, however, I knew I had to make flag2 true to proceed. Putting a breakpoint at line 11 (referring to the image below), I discovered I could just simply edit the value of flag2 in dnSpy to be true and once I did that, the if check passed and the program went on to 2().
While stepping through 2(). On line 36, I was surprised to find this very important looking string.
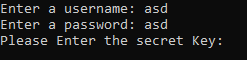
The line after that asked me for this very secret key:
Putting our key in and stepping through the rest of the program, we get our HTB flag!
Concluding thoughts
This challenge was fairly easy and fun (not going to dive into medium/hard ones just yet), and I hope to do more reversing challenges soon!